DevSecOps Security Tools: SAST, DAST, SCA, Monitoring
Modern software development requires not only speed but also security. DevSecOps integrates security practices into every stage of the CI/CD pipeline, ensuring that vulnerabilities are detected and mitigated as early as possible.
This guide covers the main types of security tools—SAST, DAST, SCA (Dependency Scanning), Monitoring/Observability, and the OWASP Top 10 security risks.
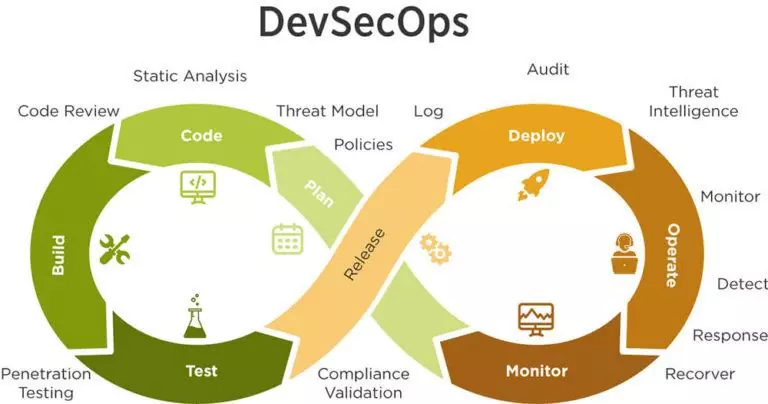
1. What is SAST (Static Application Security Testing)?
SAST analyzes source code or compiled code for vulnerabilities without executing the application. It identifies insecure coding patterns early in the development lifecycle, this will be use before the building and check the source code, byte code or binaries without executing the application.

Common Findings
- SQL Injection
- Cross-site scripting (XSS)
- Hardcoded credentials
- Insecure API usage
- Missing input validation
Advantages and Disadvantages
| Advantages | Disadvantages |
|---|---|
| Detects issues early in development | May produce false positives |
| Integrates with IDEs and CI/CD pipelines | Cannot detect runtime issues |
| Supports multiple languages | Can be slower on large projects |
Common SAST Tools
- SonarQube / SonarCloud *my preference
- GitHub CodeQL
- Checkmarx
- Veracode SAST
- Fortify SCA
- Semgrep (open source)
When It Runs
Typically runs during build or pre-commit stages in CI/CD.
2. What is DAST (Dynamic Application Security Testing)?
DAST tests a running web application by simulating real-world attacks. It scans deployed endpoints for security vulnerabilities without access to the source code. Dast can scan web application or api endpoints following the tools you will be using.
Common Findings
- SQL Injection
- XSS
- Authentication bypass
- CSRF
- Security misconfigurations
- Insecure HTTP headers
Advantages and Disadvantages
| Advantages | Disadvantages |
|---|---|
| Tests actual runtime behavior | Requires a running environment |
| Detects configuration and deployment flaws | May not catch logic flaws |
| Language-independent | Slower than static analysis |
Common DAST Tools
Open Source:
- OWASP ZAP favorite
- Wapiti
- Nikto
- DalFox
- w3af
Commercial:
- Bright Security (NeuraLegion) favorite
- StackHawk
- Burp Suite Enterprise
- Netsparker (Invicti)
- Acunetix
When It Runs
Typically runs during staging or post-deploy phases, once the application is live in a testing environment like dev,qa, staging,…
3. What is SCA (Software Composition Analysis / Dependency Scanning)?

SCA scans dependencies and open-source libraries for known vulnerabilities, license risks, and outdated versions.
Most modern applications rely heavily on open-source components, making SCA a critical part of DevSecOps.
Common SCA Tools
- Snyk favorite
- Dependabot (GitHub built-in)
- WhiteSource (Mend.io)
- Anchore
- Trivy favorite
- OWASP Dependency-Check
When It Runs
Typically runs during build or dependency installation, before the final deployment.
4. Monitoring and Observability Tools
Monitoring tools provide visibility into runtime behavior, errors, and performance issues. While not vulnerability scanners, they play a vital role in detecting anomalies and ensuring secure operations.

Common Tools
| Tool | Type | Main Purpose |
|---|---|---|
| Sentry | Error and crash tracking | Real-time stack traces and release monitoring |
| Datadog | Observability platform | Logs, metrics, and performance monitoring |
| New Relic | Application Performance Monitoring (APM) | Performance analytics and uptime |
| Prometheus + Grafana | Open-source monitoring | Metrics collection and visualization |
| Elastic (ELK Stack) | Log analysis | Event correlation and anomaly detection |
When It Runs
Continuously in production environments.
5. Infrastructure as Code (IaC) Security Scanning
What Is IaC Security?
Infrastructure as Code (IaC) defines and manages cloud infrastructure (servers, networks, databases, IAM policies) using configuration files such as Terraform, AWS CloudFormation, or Kubernetes YAML manifests.
IaC Security Scanning ensures that these configurations follow security best practices and compliance standards before deployment.
It helps prevent misconfigurations that could expose critical cloud resources, such as public S3 buckets, overly permissive IAM roles, or unencrypted databases.
Why IaC Scanning Matters
Cloud breaches often occur due to misconfigurations, not code bugs.
IaC scanning detects these early by integrating into the build pipeline.
Common IaC Vulnerabilities
- Publicly exposed storage buckets (S3, Azure Blob)
- Missing encryption at rest or in transit
- Hardcoded secrets in Terraform variables
- Overly broad IAM permissions (
"*"access) - Missing resource tagging or auditing
- Unrestricted inbound security groups (0.0.0.0/0)
Popular IaC Security Tools
| Tool | Type | Description |
|---|---|---|
| Checkov | Open-source | Scans Terraform, CloudFormation, Kubernetes, and ARM templates for security issues |
| Terraform Cloud / Sentinel | Policy as Code | Enforces custom policies before infrastructure deployment |
| tfsec | Open-source | Static analysis for Terraform security and compliance |
| Bridgecrew / Prisma Cloud | Commercial | Cloud-native security suite integrating IaC, runtime, and compliance |
| kics (Keep Infrastructure as Code Secure) | Open-source | Detects vulnerabilities in Terraform, Kubernetes, and Dockerfiles |
| AWS Config / Azure Policy / GCP Security Scanner | Native cloud services | Monitor and enforce compliance in live environments |
When It Runs
IaC scanning runs before deployment, typically in:
- CI/CD pipelines (e.g., GitHub Actions, GitLab CI)
- Pull request validation
- Pre-commit hooks (using tools like
pre-commitandtfsec)
6. How These Tools Fit Together
| Stage | Type | Goal | Example Tools |
|---|---|---|---|
| Pre-Commit / Early Development | SAST | Detect insecure code | SonarQube, CodeQL, Semgrep |
| Build / Dependency Installation | SCA | Detect vulnerable dependencies | Snyk, Dependabot, Trivy |
| Post-Build / Staging | DAST | Detect runtime vulnerabilities | OWASP ZAP, Bright, StackHawk |
| Pre-Release | IaC / Container Security | Secure infrastructure and containers | Checkov, Prisma Cloud, Aqua |
| Production | Monitoring | Observe live performance and errors | Sentry, Datadog, New Relic |
Conclusion

Integrating security throughout the software development lifecycle is no longer optional. It’s a necessity !
Modern DevSecOps practices ensure that applications, infrastructure, and deployments are secure from the very first line of code to production monitoring.
By combining tools and methodologies across SAST, SCA, DAST, IaC, container, and Kubernetes security, organizations can achieve continuous assurance and resilience in their cloud-native environments.
Security should not slow down development. Instead, it should act as a quality enabler, embedded into every phase of the CI/CD pipeline. Automated scans, policy enforcement, and runtime monitoring allow teams to detect and fix vulnerabilities earlier—reducing risk and cost.
A mature DevSecOps pipeline looks like a unified workflow where developers, security engineers, and operations teams share a common goal, to deliver secure, stable, and reliable software at speed and scale.
In the end, the most secure systems are not those that never fail but those that detect, respond, and recover quickly.
